Valid for OAuth2.0 Authentication Mode only.
Under IdentityServer4 Authentication Mode, Identity Resources are configured in the IdentityServer4 server.
In OAuth2.0 they are also known as Resource Owners.
The owner of the resource is the user who gives authorization to a certain application to access his account and be able to do some things on his behalf.
The set of things the application can do on its behalf is defined by Scopes, and could be, for example, read only access and not being able to create any type of element from any new resource.
Identity Resources define data such as the user ID, name or email address. An Identity Resource has an unique name and can be assigned arbitrary Claims. These Claims will be included in the user's identity token. The client will use the scp parameter to request access to an Identity Resource.
We will define the list of users together with their Claims. The administrator has the option to have an MVBASIC subroutine managing the users. More information about MV components here.
Field
|
Type
|
Description
|
New
|
Button
|
Create Identity Re-source.
|
Delete Selected
|
Button
|
Delete selected Identity Resources from the Database.
|
Export Selected
|
Button
|
Export selected Identity Resources to a JSON file.
|
Import from file
|
Button
|
Import Identity Resources from a JSON file.
|
Pencil Icon
|
Button
|
Edit Identity Resource.
|
Trash Icon
|
Button
|
Delete Identity Resource.
|
Copy Icon
|
Button
|
Create Identity Resource by copying data from an existing Identity Resource.
|
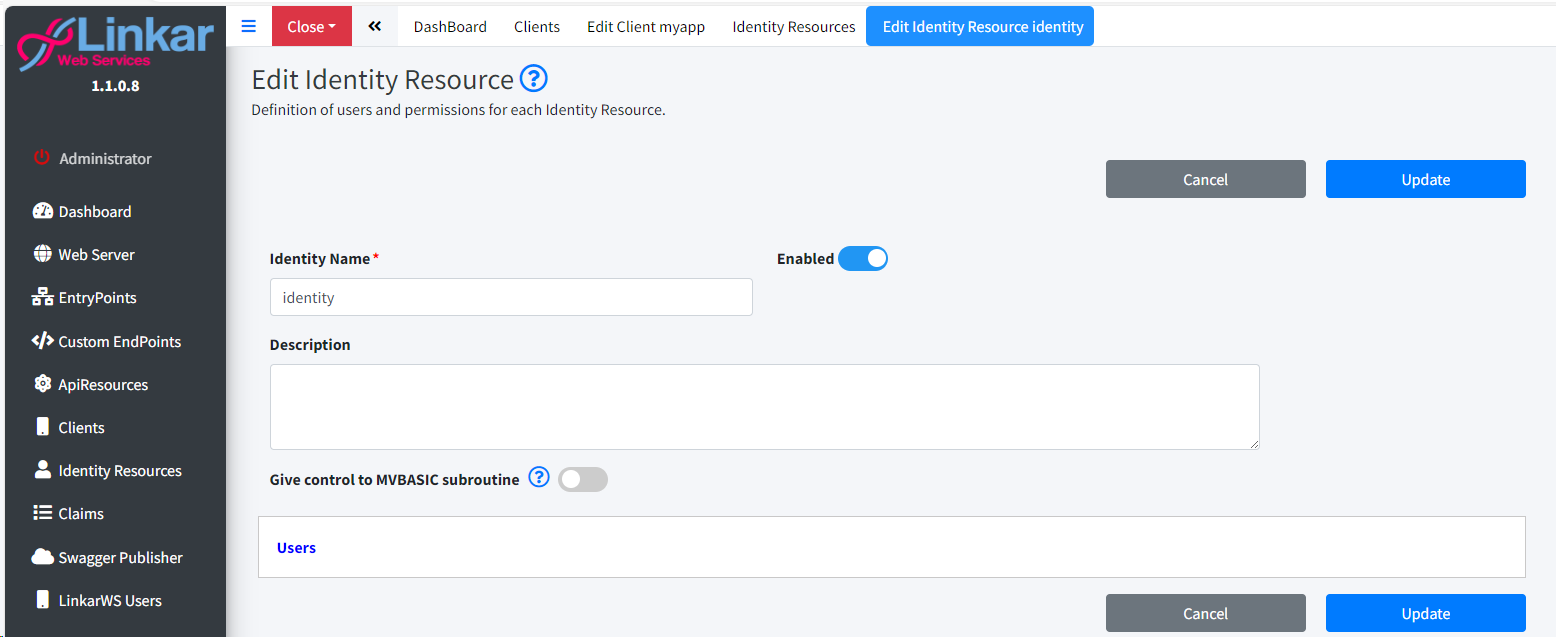
 Create/Edit/Copy Identity Resource
Create/Edit/Copy Identity Resource
|
Field
|
Type
|
Description
|
Cancel
|
Button
|
Discard changes and close the form.
|
Create/Update
|
Button
|
Save IdentityResource.
|
Identity Name
|
Required
|
Unique name for the Identity Resource. The client will use this value for the Scope parameter in the authorization request.
|
Enabled
|
Switch
|
Enable or disable Identity Resource.
|
Description
|
Optional
|
Internal description for documentation.
|
Give control to MVBASIC subroutine
|
Switch
|
The administrator can use the SUB.LK.MAIN.WS.IDENTITY.RESOURCES routine to manage and control the users. This routine must validate and return the Claims assigned to the user. Link to MVComponents.
|
Linkar EntryPoint
|
Select
|
In case of giving control to the MVBasic subroutine, we will have to indicate in which EntryPoint this sub-routine is located.
|
|
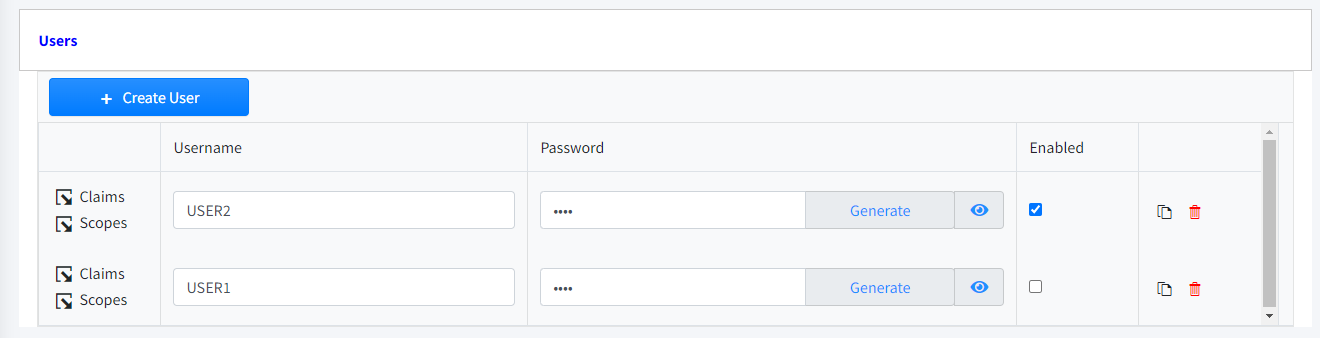
 Users
Users
It’s necessary to define users if the Clients use Resource Owner Password as Grand Type for authentication. Otherwise there is no need to define users.
In case we do not use the MVBasic subroutine provided by LinkarWS, we will have to register all the users and their parameters through Claims.
Field
|
Type
|
Description
|
Username
|
Required
|
Name or id of the user.
|
Password
|
Required
|
User password.
|
Enabled
|
Checkbox
|
Enables/disables user.
|
|
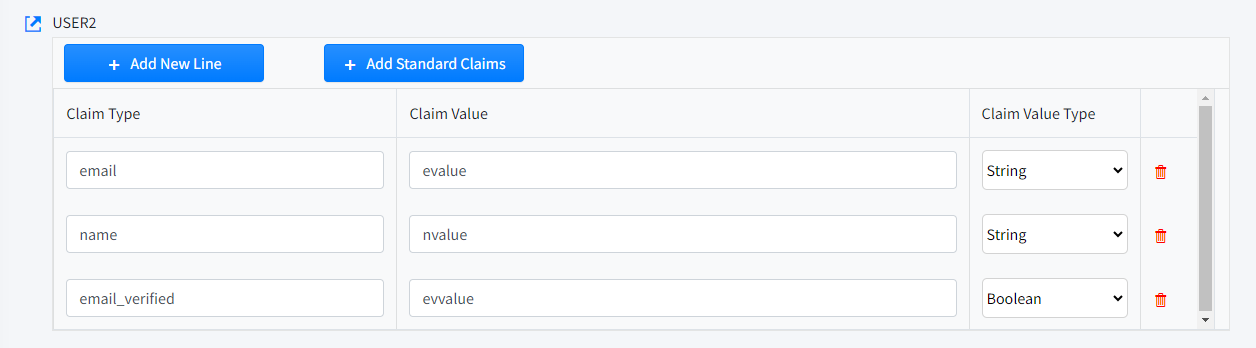
 User Claims
User Claims
Definition of the User Claims passed in the token.
Field
|
Type
|
Description
|
Add Claim
|
Button
|
Add new Claim.
|
Copy Standard Claims
|
Button
|
Adds all Standard Claims assigned to users.
|
Claim Type
|
Required
|
Claim Name.
|
Claim Value
|
Required
|
Claim Value.
|
Claim Value Type
|
Select
|
String, Boolean, Numeric or JSON value type.
|
|
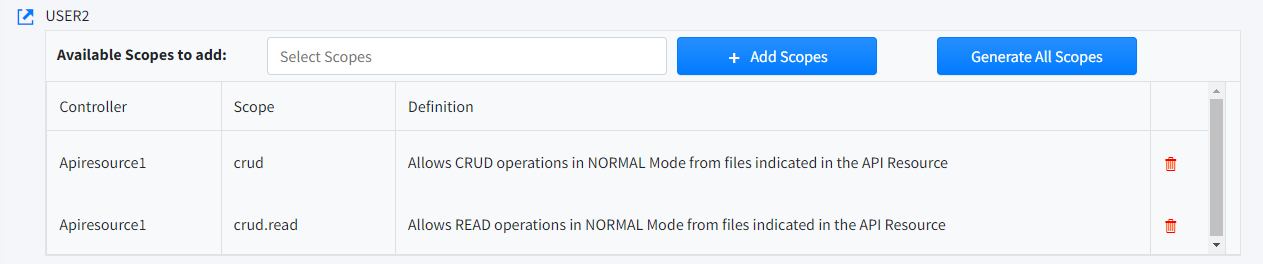
 User Scopes
User Scopes
Through Scopes we filter and define the different resources allowed to the User. You can assign any or all of the Scopes defined in the different existing API Resources.
Field
|
Type
|
Description
|
Available Scopes to add
|
Select
|
Select one or more Scopes.
|
Add Scopes
|
Button
|
Add selected Scope.
|
Generate All Scopes
|
Button
|
Add all available Scopes.
|
|
 Create/Edit/Copy Identity Resource
Create/Edit/Copy Identity Resource